**In an increasingly interconnected world, the ability to manage and monitor devices remotely is not just a convenience; it's a fundamental necessity. From smart homes to industrial complexes, the Internet of Things (IoT) has revolutionized how we interact with our environment, creating vast networks of intelligent devices. Yet, with great connectivity comes great responsibility, particularly concerning security and accessibility. This is where remoteiot web ssh free solutions emerge as a critical enabler, offering a secure, efficient, and often cost-effective pathway to manage your IoT ecosystem from anywhere on the globe.**
Imagine a bustling historical street, vibrant with activity, constantly evolving through centuries, much like Beijing's Dashilan. It adapted from ancient night bans to a commercial hub, enduring fires and transformations, always finding new ways to connect people and commerce. Similarly, in the digital realm, we need robust, adaptable, and secure pathways. Traditional methods of device management, often requiring physical presence or complex network configurations, are becoming relics of the past. The demand for seamless, secure remote access to IoT devices has never been higher, and Web SSH is stepping up to meet this challenge, providing the digital equivalent of a well-established, trustworthy thoroughfare for your data and commands.
Table of Contents
- The Evolution of Remote Access: From Old Streets to Digital Highways
- Understanding Remote IoT: The Backbone of Modern Connected Systems
- Why SSH is Indispensable for Remote IoT Management
- Unlocking Freedom: The "Web SSH Free" Advantage
- Setting Up Your Secure Remote IoT Connection: A Practical Guide
- Best Practices for Fortifying Your Remote IoT Security
- Real-World Applications and Use Cases of Remote IoT Web SSH
- Navigating the Future: Trends and Innovations in Remote IoT Access
The Evolution of Remote Access: From Old Streets to Digital Highways
Just as historical districts like Dashilan transformed over centuries from simple barriers (栅栏) into bustling commercial centers, adapting to new eras and technologies, so too has the concept of remote access evolved. In ancient times, "night bans" and physical barriers dictated movement and commerce. Later, established thoroughfares and specialized shops became the arteries of trade. This organic growth, sometimes interrupted by challenges like the 1900 fire that consumed Dashilan's wooden gate, mirrors the journey of digital connectivity. Initially, remote access was cumbersome, often requiring dedicated lines, complex VPNs, or physical presence. It was like navigating unpaved roads in the dark, fraught with security risks and inefficiencies.
- Kim Basinger 2022
- Remote Iot P2p Download Mac
- Jameliz Benitez Smith Biography
- Gia Lovers Erome
- Subhashree Sahu Video Leak
With the advent of the internet, the digital landscape began to resemble a sprawling city, demanding more sophisticated and secure pathways. The need for a universally accessible, secure shell (SSH) protocol became evident. SSH provided the foundational "iron gate" – much like the iron art fence rebuilt at Dashilan's entrance in 2000 – a robust, secure entry point. Now, with the proliferation of IoT devices, the challenge has escalated. We're no longer just connecting a few computers; we're connecting millions, even billions, of tiny, distributed sensors and actuators. This vast network necessitates a solution that is not only secure but also incredibly flexible and easy to deploy. This is precisely where remoteiot web ssh free services step in, offering a modern, browser-based solution that combines the ubiquity of the web with the ironclad security of SSH, paving a new digital highway for IoT management.
Understanding Remote IoT: The Backbone of Modern Connected Systems
Remote IoT refers to the capability of interacting with Internet of Things devices from a location other than where the device physically resides. This interaction can range from monitoring sensor data and issuing commands to performing firmware updates and troubleshooting. Imagine a network of smart streetlights across a city, or environmental sensors deployed in remote agricultural fields, or even critical machinery in a factory on the other side of the world. Each of these scenarios benefits immensely from remote management, reducing operational costs, improving efficiency, and enabling rapid response to issues.
The core components of a remote IoT setup typically include the IoT device itself (often a small, low-power computer like a Raspberry Pi or ESP32), a network connection (Wi-Fi, cellular, LoRaWAN, etc.), and a remote management platform or tool. Without effective remote access, managing a large-scale IoT deployment would be logistically impossible and financially prohibitive. Think of the historical challenges of managing a vast empire without efficient communication lines – the modern equivalent for IoT is the need for reliable, secure remote access. This is where solutions like remoteiot web ssh free become indispensable, providing the necessary infrastructure for seamless operation.
Why SSH is Indispensable for Remote IoT Management
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its primary use is for remote command-line login and remote command execution. For IoT devices, many of which run Linux-based operating systems, SSH provides a robust and secure method for direct interaction. It encrypts all traffic, including passwords, commands, and data, protecting against eavesdropping, connection hijacking, and other network-level attacks. This level of security is paramount, especially for YMYL (Your Money or Your Life) applications where device compromise could lead to significant financial loss, data breaches, or even physical harm.
Consider the sensitive nature of data collected by IoT devices – from personal health metrics to industrial control signals. An unsecured connection is an open invitation for malicious actors. SSH mitigates this risk by:
- Encryption: All data exchanged between the client and the server is encrypted, making it unreadable to unauthorized parties.
- Authentication: SSH supports strong authentication methods, including password-based and public-key authentication, ensuring only authorized users can access devices.
- Integrity: It verifies the integrity of the data to ensure it hasn't been tampered with during transmission.
- Port Forwarding/Tunneling: SSH can securely tunnel other network services, allowing for secure access to services that might otherwise be exposed.
Unlocking Freedom: The "Web SSH Free" Advantage
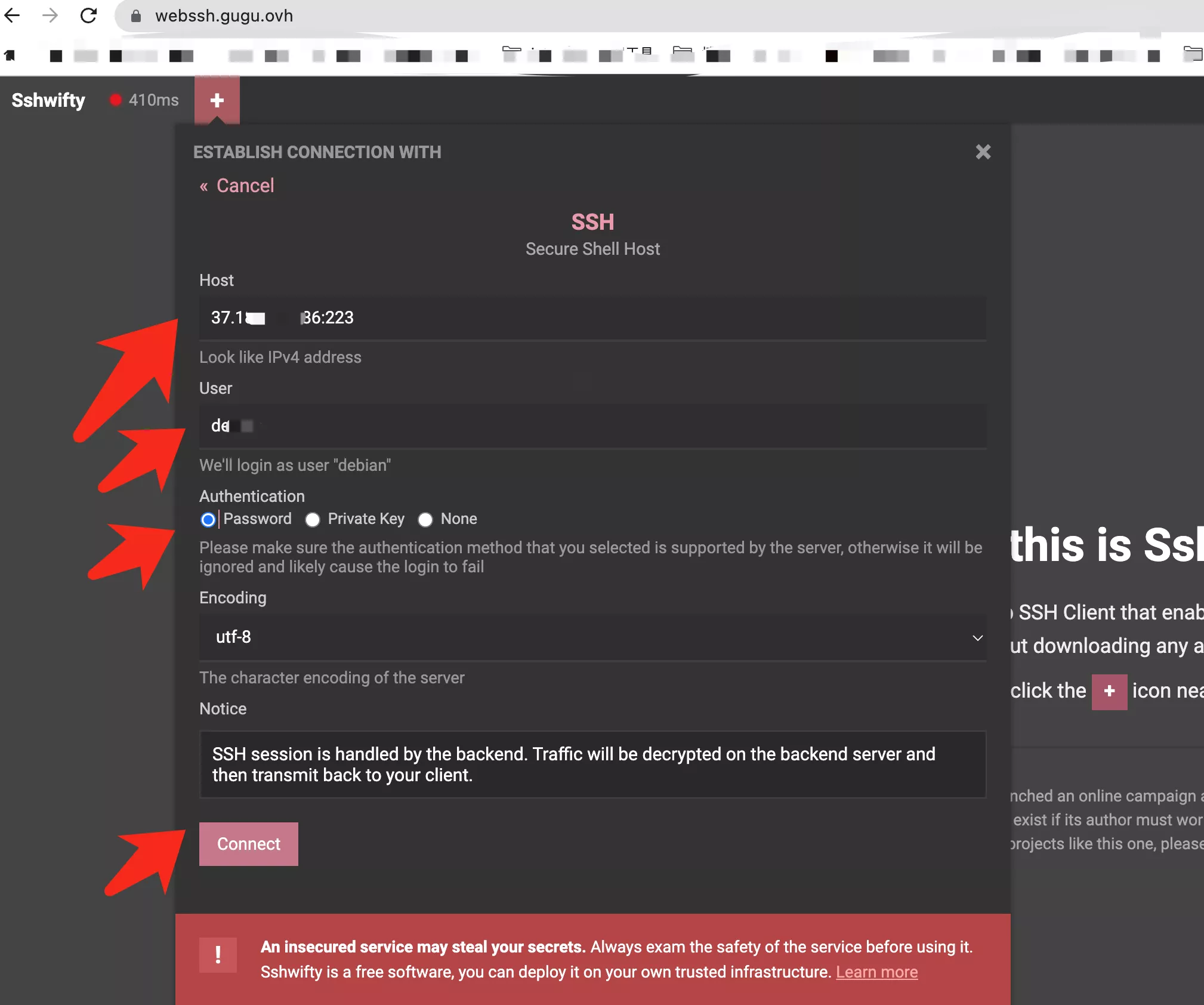
The "Web SSH Free" paradigm represents a significant leap forward in remote IoT management. Traditionally, accessing SSH required a dedicated client application installed on your computer. While effective, this could be cumbersome for quick checks, or when working from a device where you don't have administrative privileges to install software. Web SSH, on the other hand, allows you to establish an SSH connection directly from your web browser. This eliminates the need for client software, making remote access incredibly convenient and platform-agnostic. Whether you're on a laptop, tablet, or even a smartphone, as long as you have a web browser, you can connect.
The "free" aspect often refers to services that provide a basic tier of Web SSH connectivity without charge, or open-source solutions that can be self-hosted. This accessibility is crucial for hobbyists, startups, and even larger organizations looking to experiment or manage smaller deployments without initial investment. The benefits are manifold:
- Accessibility: Connect from any device with a web browser, anywhere, anytime.
- No Software Installation: Reduces setup time and avoids compatibility issues.
- Cost-Effective: Many free tiers or open-source options are available.
- Simplified Troubleshooting: Rapidly diagnose and resolve issues without needing to be physically present.
Setting Up Your Secure Remote IoT Connection: A Practical Guide
Establishing a secure remoteiot web ssh free connection involves a few key steps, ensuring both accessibility and robust security. This process is similar to how ancient cities would establish secure entry points, like the gates of Dashilan, ensuring only authorized individuals could pass while maintaining order and security.
Prerequisites for Seamless Integration
- IoT Device with SSH Server: Your IoT device (e.g., Raspberry Pi, BeagleBone Black) must have an SSH server (like OpenSSH) installed and running. Most Linux-based IoT distributions include this by default.
- Network Connectivity: The IoT device needs to be connected to the internet, either directly or via a local network with appropriate port forwarding configured on the router. For enhanced security, consider using a VPN or a specialized IoT connectivity platform that creates secure tunnels without exposing ports directly.
- Public IP Address or DNS Service: To access your device from anywhere, it needs a public IP address, or you'll need to use a Dynamic DNS (DDNS) service if its IP changes frequently. Many remoteiot web ssh free services offer their own tunneling solutions, circumventing the need for direct public IP exposure, which is a significant security advantage.
- SSH Keys (Recommended): While password authentication is possible, SSH key-based authentication is far more secure. Generate a pair of SSH keys (public and private) on your local machine and copy the public key to your IoT device.
Step-by-Step Connection Process
- Prepare Your IoT Device:
- Ensure SSH is enabled. For Raspberry Pi, you can enable it via `sudo raspi-config`.
- Update your system: `sudo apt update && sudo apt upgrade`.
- (Optional but Recommended) Set up SSH key authentication:
- Generate keys on your local machine: `ssh-keygen -t rsa -b 4096`.
- Copy public key to IoT device: `ssh-copy-id user@your_device_ip`.
- Choose a Web SSH Service: Research and select a reputable remoteiot web ssh free provider. Examples include services offered by cloud providers, dedicated IoT platforms, or open-source solutions like GateOne or Shell In A Box that you can self-host. Prioritize those that emphasize security, uptime, and privacy.
- Configure the Web SSH Service: Follow the specific instructions of your chosen service. This typically involves:
- Creating an account.
- Adding your IoT device's IP address (or hostname) and SSH port (default is 22).
- Configuring authentication (username/password or, preferably, pasting your private SSH key into the service's secure interface).
- If the service uses a tunneling agent, install that agent on your IoT device. This is often the most secure method as it initiates an outbound connection, bypassing inbound firewall rules.
- Connect from Your Browser: Navigate to the Web SSH service's portal in your browser, select your device, and initiate the connection. You should see a command-line interface directly in your browser, allowing you to interact with your IoT device as if you were physically connected.
Always remember to secure your Web SSH service account with a strong, unique password and enable multi-factor authentication (MFA) if available. The security of your entire IoT ecosystem hinges on the weakest link, and your access method is a critical one.
Best Practices for Fortifying Your Remote IoT Security
While remoteiot web ssh free offers unparalleled convenience, the "free" aspect should never imply a compromise on security. In fact, due to the remote nature and the potential for widespread impact, IoT security demands even greater vigilance. Just as the old shops of Dashilan, like Quanjude or Yue Sheng Zhai, built their reputations on trust and quality over centuries, your remote IoT infrastructure must be built on a foundation of robust security practices to earn and maintain trust. Ignoring security is like leaving your valuable goods out in the open on a busy street – an invitation for trouble.
Beyond Passwords: Multi-Factor Authentication (MFA)
Passwords, even strong ones, can be compromised. Multi-Factor Authentication (MFA) adds additional layers of security, typically requiring something you know (password), something you have (a phone or hardware token), and/or something you are (biometrics). For remote SSH access:
- SSH Key Authentication: This is the strongest form of authentication for SSH. Disable password authentication on your IoT devices entirely once SSH keys are set up.
- MFA for Web SSH Platform: If your Web SSH provider offers MFA for logging into their portal, enable it immediately. This protects your gateway to all your devices.
- PAM Modules for SSH: For advanced users, configure Pluggable Authentication Modules (PAM) on your IoT device to enforce MFA directly for SSH logins (e.g., using Google Authenticator for a TOTP code).
Regular Audits and Firmware Updates
The digital world is constantly evolving, with new vulnerabilities discovered daily. Staying ahead of threats requires proactive measures:
- Keep Software Updated: Regularly update the operating system, SSH server, and any other software on your IoT devices. This patches known vulnerabilities. `sudo apt update && sudo apt upgrade` is your friend.
- Firmware Updates: Ensure your IoT device's firmware is always the latest version from the manufacturer. Firmware often contains critical security patches.
- Security Audits: Periodically review your SSH configurations (e.g., `sshd_config` file), user accounts, and network settings. Remove unnecessary services or open ports. Consider using security scanning tools.
- Log Monitoring: Regularly check SSH logs (`/var/log/auth.log` on Linux) for suspicious login attempts or activities.
- Principle of Least Privilege: Create separate user accounts for different tasks and grant them only the minimum necessary permissions. Avoid using the 'root' user for daily operations.
Real-World Applications and Use Cases of Remote IoT Web SSH
The practical applications of remoteiot web ssh free are vast and impactful, touching almost every sector where IoT devices are deployed. This technology is not just about convenience; it's about enabling new business models, improving operational efficiency, and ensuring continuity in critical systems. Just as Dashilan became a hub for diverse businesses, from traditional medicine shops to famous restaurants, remote IoT with Web SSH is becoming the central nervous system for a multitude of connected operations.
- Smart Agriculture: Farmers can remotely monitor soil conditions, irrigation systems, and livestock health from their homes or offices. If a sensor malfunctions or a drone needs a new flight path, SSH allows for immediate diagnostics and command execution, saving valuable time and resources.
- Industrial IoT (IIoT): In factories and industrial plants, remote SSH enables engineers to access PLCs, sensors, and robotic arms for troubleshooting, predictive maintenance, and software updates without needing to be physically on the factory floor. This is critical for minimizing downtime and ensuring worker safety.
- Smart Cities: Managing networks of smart streetlights, waste management sensors, or traffic cameras across a large urban area becomes feasible. City administrators can remotely configure devices, pull data logs, or restart services, enhancing urban efficiency and responsiveness.
- Home Automation and Security: For advanced smart home users, SSH provides direct access to home automation hubs (like Home Assistant on a Raspberry Pi) to customize settings, install plugins, or diagnose network issues. This offers a level of control beyond standard apps.
- Remote Research and Education: Scientists and students can access remote lab equipment, weather stations, or experimental setups for data collection and analysis, regardless of their geographical location. This democratizes access to resources and fosters collaboration.
- Retail and Commercial Spaces: Managing digital signage, point-of-sale systems, or environmental controls across multiple retail locations. A quick SSH session can resolve software glitches or update content, ensuring smooth operations.
Navigating the Future: Trends and Innovations in Remote IoT Access
The trajectory of remote IoT access is one of continuous innovation, driven by the increasing
Related Resources:

Detail Author:
- Name : Martine Cole
- Username : wolf.adonis
- Email : hchristiansen@brown.com
- Birthdate : 1996-09-02
- Address : 4986 Jessika Lane Apt. 287 West Darenshire, HI 88785-5269
- Phone : +1-608-495-0944
- Company : Koepp, Schoen and Maggio
- Job : Pastry Chef
- Bio : Eos et in numquam odit officia. Deleniti ad exercitationem rem et vero. Quisquam delectus rerum nobis debitis voluptates. Corporis eum sit iste exercitationem qui voluptatem.
Socials
instagram:
- url : https://instagram.com/arielle_ondricka
- username : arielle_ondricka
- bio : Ullam inventore vero ex qui modi quis. Temporibus eius doloremque voluptate omnis aut.
- followers : 5134
- following : 1263
twitter:
- url : https://twitter.com/aondricka
- username : aondricka
- bio : Quo similique eos neque perspiciatis vel tempore sunt. Quas eos ut id deserunt distinctio. Delectus repudiandae quo et omnis.
- followers : 1337
- following : 1853