In the rapidly expanding world of the Internet of Things (IoT), the Raspberry Pi stands out as a versatile and powerful single-board computer, enabling countless innovative projects. Central to managing and securing these projects, especially when deployed remotely, is Secure Shell (SSH). Understanding how to effectively utilize SSH with your Raspberry Pi is not just a convenience; it's a fundamental security practice that empowers you to control, monitor, and troubleshoot your IoT devices from virtually anywhere. This comprehensive guide will delve deep into the world of SSH Raspberry Pi IoT projects, exploring everything from basic setup to advanced security configurations and practical applications.
Whether you're building a smart home automation system, a remote sensor network, or an environmental monitoring station, the ability to securely access your Raspberry Pi is paramount. SSH provides an encrypted channel for command-line access, file transfers, and even tunneling, making it an indispensable tool for any IoT enthusiast or professional. We'll navigate the intricacies of SSH, address common challenges, and provide insights that will help you build robust and secure IoT solutions, ensuring your projects are not only functional but also protected against potential vulnerabilities.
Table of Contents
- What is SSH and Why It Matters for IoT?
- Initial Setup: Enabling SSH on Your Raspberry Pi
- Securing Your SSH Connection: Best Practices
- Advanced SSH Configurations and Troubleshooting
- Practical SSH Raspberry Pi IoT Projects Ideas
- Monitoring and Managing Your IoT Devices Remotely
- Common SSH Challenges and Solutions in IoT
- The Future of SSH in IoT Security
What is SSH and Why It Matters for IoT?
SSH, or Secure Shell, is a cryptographic network protocol for operating network services securely over an unsecured network. Its primary function is to provide a secure channel over an unsecured network in a client-server architecture, connecting an SSH client with an SSH server. For Raspberry Pi IoT projects, SSH is the backbone of remote management. Imagine deploying a Raspberry Pi in a remote location – perhaps monitoring a garden's soil moisture, controlling outdoor lighting, or collecting weather data. Without SSH, physically accessing the device for updates, troubleshooting, or data retrieval would be a constant logistical nightmare. SSH encrypts all traffic between the client and the server, protecting sensitive information like usernames, passwords, and command outputs from eavesdropping. This is crucial in IoT, where devices might be connected to public or less secure networks. Beyond basic command-line access, SSH can also be used for secure file transfers (SFTP/SCP), port forwarding, and even creating secure tunnels for other applications. The security and flexibility offered by SSH make it an indispensable tool for any serious SSH Raspberry Pi IoT projects developer, ensuring that your remote devices remain under your control and their data stays private.Initial Setup: Enabling SSH on Your Raspberry Pi
Enabling SSH on a Raspberry Pi is a straightforward process, but it's often the first step in setting up any remote IoT project. When you first install Raspberry Pi OS, SSH might not be enabled by default for security reasons. There are several ways to enable it: 1. **Using `raspi-config` (Desktop or Headless):** * Boot your Raspberry Pi. * Open a terminal and type `sudo raspi-config`. * Navigate to `Interface Options` -> `SSH` -> `Yes`. * Reboot your Pi. 2. **Creating an `ssh` file (Headless setup):** * Before booting your Raspberry Pi for the first time, insert the SD card into your computer. * In the `boot` partition of the SD card, create an empty file named `ssh` (no extension). * When the Raspberry Pi boots, it will detect this file and enable SSH automatically. For enhanced security, consider also creating a `userconf` file to set up a new user with a strong password, avoiding the default `pi` user. Once SSH is enabled, you can connect from another computer on the same network using an SSH client (like PuTTY on Windows, or the built-in terminal on Linux/macOS). The basic command is `ssh pi@your_raspberry_pi_ip_address`. You'll be prompted for the password for the `pi` user (default: `raspberry`). For instance, if your Pi's IP is `192.168.1.100`, you'd type `ssh pi@192.168.1.100`. This initial connection is your gateway to managing your SSH Raspberry Pi IoT projects.Securing Your SSH Connection: Best PracticesChanging the Default SSH Port
By default, SSH operates on port 22. This is widely known, making it a common target for automated scanning tools and brute-force attacks. One of the simplest yet effective security measures is to change the default SSH port to a non-standard, high port number (e.g., anything above 1024, like 2222, 22222, or 49152). As one of the provided insights mentions, "The ssh server you are attempting to connect to will have sshd running on one port and that need not be 22, Many servers move ssh to a high port to cut down on the number of." This significantly reduces the noise from automated scans, as attackers typically target well-known ports. To change the port: 1. SSH into your Raspberry Pi. 2. Edit the SSH daemon configuration file: `sudo nano /etc/ssh/sshd_config`. 3. Find the line `#Port 22`. Uncomment it (remove the `#`) and change `22` to your desired port number (e.g., `Port 2222`). 4. Save the file and exit. 5. Restart the SSH service: `sudo systemctl restart ssh`. Now, when connecting, you'll need to specify the new port: `ssh pi@your_raspberry_pi_ip_address -p 2222`.SSH Key Authentication vs. Passwords
Relying solely on passwords for SSH authentication is generally discouraged, especially for IoT devices exposed to the internet. Passwords can be brute-forced or guessed. SSH key pairs offer a far more secure alternative. An SSH key pair consists of a public key and a private key. The public key is placed on the Raspberry Pi (server), and the private key remains securely on your local machine (client). When you attempt to connect, the server challenges your client, which then proves its identity using the private key without ever transmitting it. This method is vastly more secure because: * Private keys are typically much longer and more complex than any human-generated password. * They are resistant to brute-force attacks. * Even if an attacker gains access to your Raspberry Pi, they cannot use the public key to log in as you from another machine; they would need your private key. One user's experience highlights a common scenario: "So i need to log in to a machine using a password instead of a key, which i practically never do, Seems it should be easy but nope, ssh refuses to use anything but a key." This often happens when the server is configured to *only* allow key-based authentication, a highly recommended security posture. While "Remote ssh login password would be enough in this case" might seem convenient for quick access, for any persistent or internet-facing SSH Raspberry Pi IoT projects, keys are the way to go. To set up SSH key authentication: 1. **Generate a key pair on your local machine:** `ssh-keygen -t rsa -b 4096`. Follow the prompts; it's highly recommended to set a strong passphrase for your private key. 2. **Copy the public key to your Raspberry Pi:** `ssh-copy-id pi@your_raspberry_pi_ip_address`. This command automates placing your public key (`~/.ssh/id_rsa.pub` by default) into the `~/.ssh/authorized_keys` file on the Pi. If `ssh-copy-id` isn't available or you're using a different port, you can manually copy the content of your `id_rsa.pub` file and append it to `~/.ssh/authorized_keys` on the Pi.Disabling Password Authentication and Root Login
Once you've successfully set up SSH key authentication, you should disable password authentication entirely to prevent brute-force attacks. 1. Edit `sshd_config` again: `sudo nano /etc/ssh/sshd_config`. 2. Find the line `PasswordAuthentication yes` and change it to `PasswordAuthentication no`. 3. Restart SSH: `sudo systemctl restart ssh`. Similarly, logging in directly as the `root` user is a security risk because the `root` account has unrestricted privileges. It's best practice to disable direct root login and instead log in as a regular user (like `pi`) and use `sudo` for administrative tasks. 1. In `sshd_config`, find `PermitRootLogin yes` and change it to `PermitRootLogin no` or `PermitRootLogin prohibit-password` (which allows key-based root login but not password-based). For most IoT projects, `no` is preferred. 2. Restart SSH. One user's speculation, "I can speculate that this prevents adding your public key (which is paired with encrypted private key) without knowing," refers to the inherent security of key-based authentication. If password authentication is disabled, an attacker cannot simply add their public key to your `authorized_keys` file without first gaining access through other means (e.g., exploiting a different vulnerability), which is significantly harder.Advanced SSH Configurations and Troubleshooting
Beyond the basics, SSH offers a plethora of options for fine-tuning security and connection stability, which are particularly relevant for always-on SSH Raspberry Pi IoT projects.Maintaining Persistent SSH Connections
A common frustration for remote users is SSH sessions disconnecting due to inactivity. As observed by a user: "I have a ssh connection to a machine which gets disconnected by that machine after 30 minutes of no user input, However, if i start something like top, the connection stays alive, Since this is a c." This behavior is often due to server-side timeouts or network issues. You can configure SSH to send "keep-alive" messages to prevent disconnections. On the client side (your computer): * Edit your SSH client configuration: `nano ~/.ssh/config` (create if it doesn't exist). * Add the following lines: ``` Host * ServerAliveInterval 60 ServerAliveCountMax 3 ``` This tells your client to send a null packet to the server every 60 seconds if no data has been received from the server, and to retry 3 times before disconnecting. On the server side (Raspberry Pi): * Edit `sshd_config`: `sudo nano /etc/ssh/sshd_config`. * Add or uncomment: ``` ClientAliveInterval 300 ClientAliveCountMax 0 ``` `ClientAliveInterval 300` means the server will send a message to the client if no data has been received for 300 seconds (5 minutes). `ClientAliveCountMax 0` means it will continue sending messages indefinitely, preventing the server from closing the connection due to inactivity. Remember to restart `sshd` after changes.Understanding SSH Algorithms and Fingerprints
SSH relies on various cryptographic algorithms for key exchange (KexAlgorithms), encryption (Ciphers), and integrity checking (MACs). Modern SSH clients and servers support a wide range of these, with newer ones being more secure. When troubleshooting connection issues or aiming for maximum security, it can be useful to know which algorithms are supported. A user asks, "Is there a way to make ssh output what macs, ciphers, and kexalgorithms that it supports, I'd like to find out dynamically instead of having to look at the source." While SSH doesn't have a direct command to list *all* supported algorithms dynamically on the fly, you can inspect the `sshd_config` file on the server or use verbose client output: * **Client-side inspection:** `ssh -vvv pi@your_raspberry_pi_ip_address` will provide very verbose output, including the negotiation of algorithms. * **Server-side configuration:** The `sshd_config` file explicitly lists or implies which algorithms are enabled. You can explicitly define them for tighter security, for example: ``` KexAlgorithms curve25519-sha256@libssh.org,ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256 Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com ``` This ensures only strong, modern algorithms are used, enhancing the security of your SSH Raspberry Pi IoT projects. The "fingerprint" is another critical security concept. When you first connect to a new SSH server, you'll see a message like "The authenticity of host 'your_raspberry_pi_ip_address' can't be established. Are you sure you want to continue connecting (yes/no)?". This is followed by the server's public key fingerprint. As noted, "The fingerprint is based on the host's public key, usually based on the /etc/ssh/ssh_host_rsa_key.pub file, Generally it's for easy identification/verification of the host." You should always verify this fingerprint against the actual fingerprint on your Raspberry Pi (which you can get by running `ssh-keygen -lf /etc/ssh/ssh_host_rsa_key.pub` on the Pi). This verification prevents "man-in-the-middle" attacks where an imposter server might try to intercept your connection.Practical SSH Raspberry Pi IoT Projects Ideas
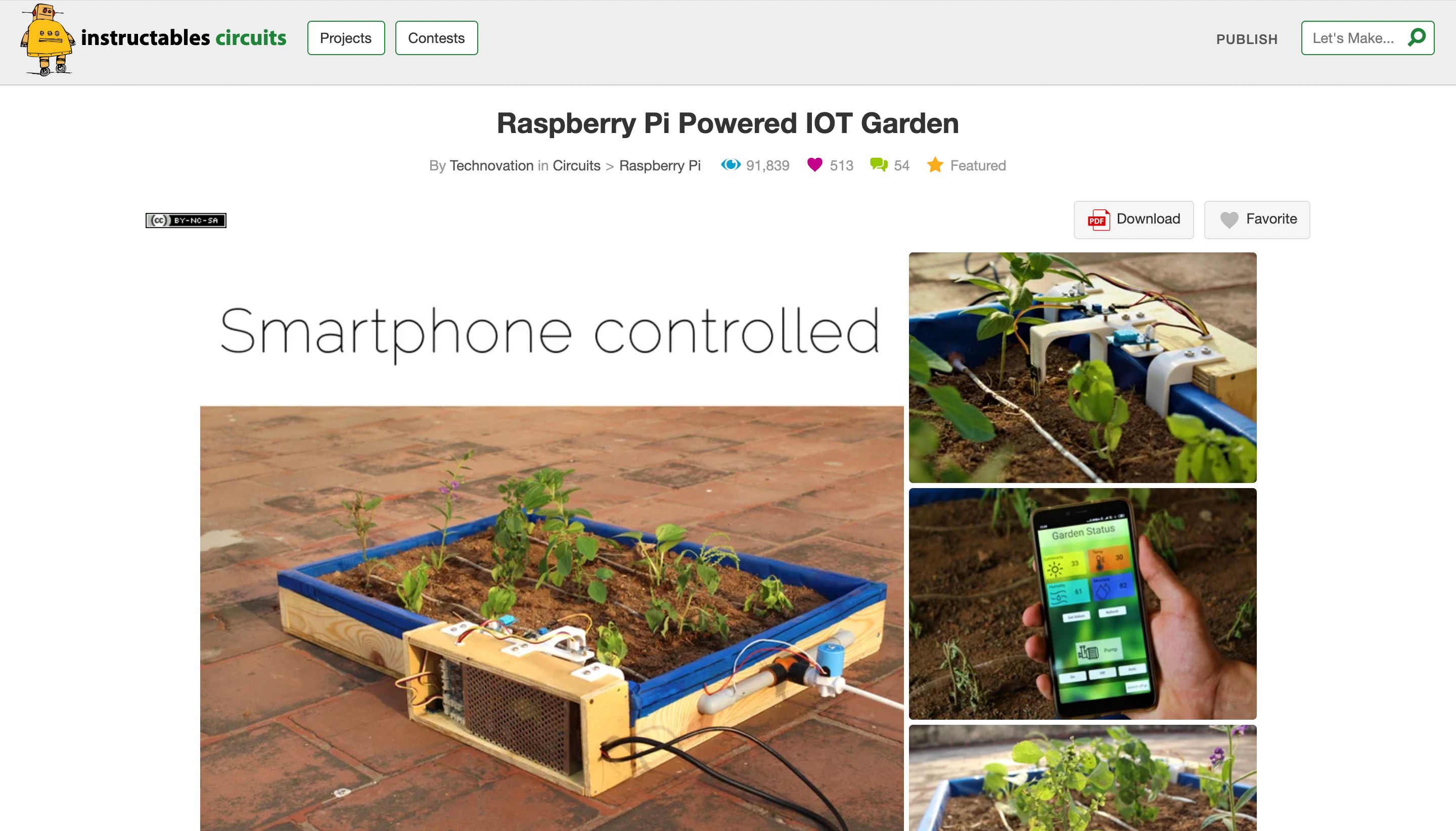
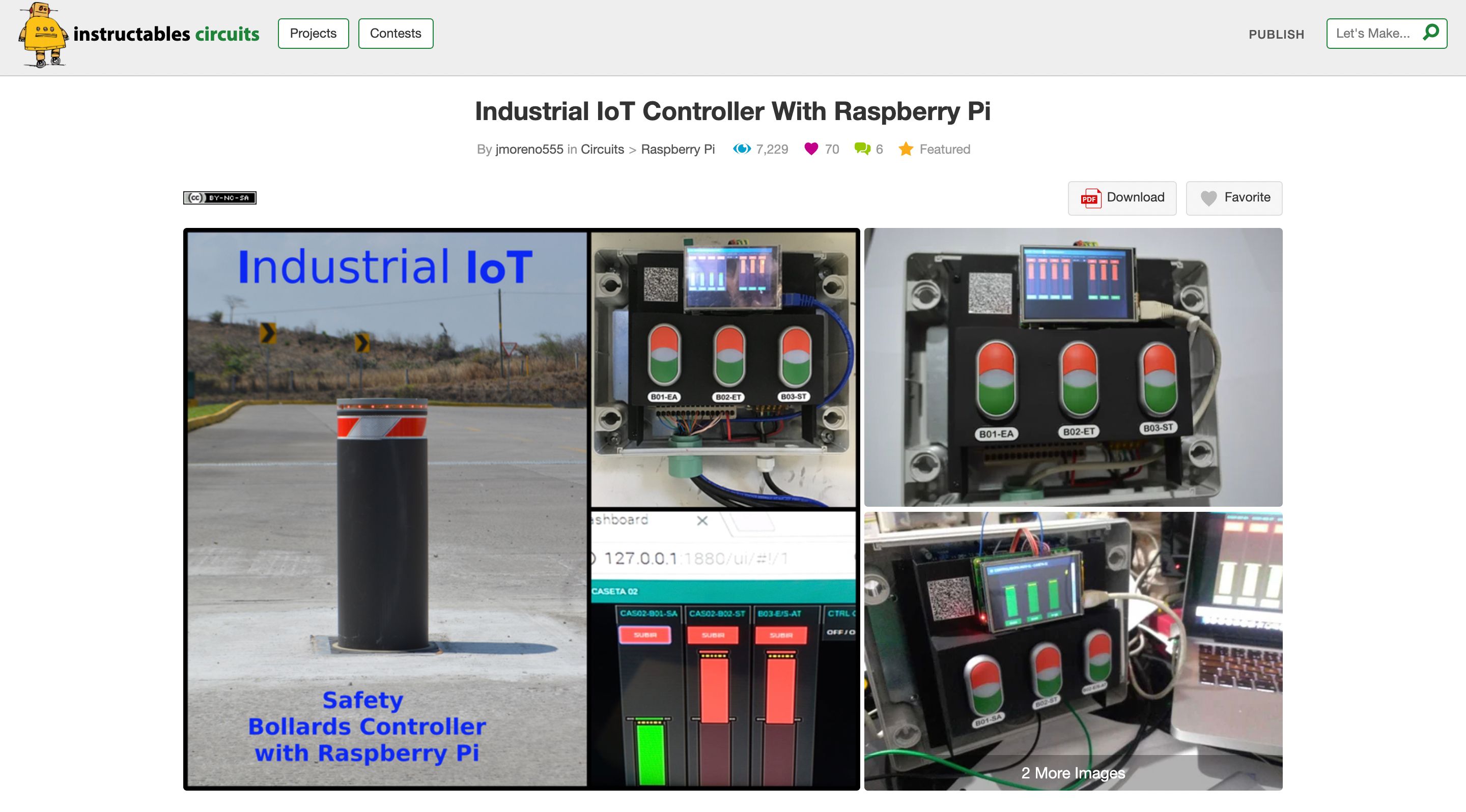
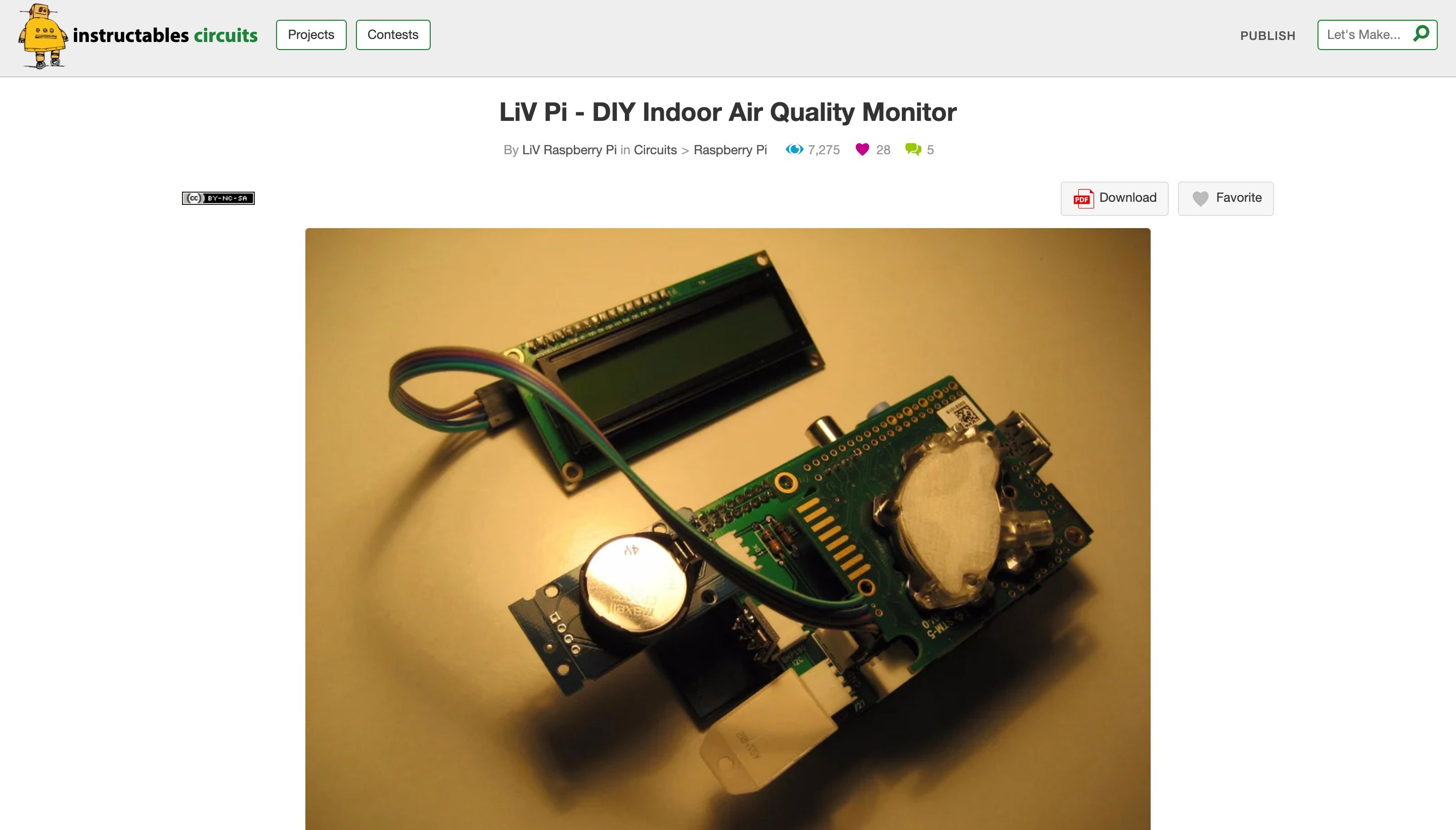
SSH transforms the Raspberry Pi into an even more powerful tool for IoT. Here are some project ideas leveraging SSH for remote management and security: * **Remote Home Automation Hub:** Control smart lights, thermostats, or security cameras from anywhere. SSH allows you to execute scripts on the Pi that interface with various smart devices, without needing a dedicated app interface. You could even set up a secure tunnel to access a local web interface. * **Environmental Monitoring Station:** Deploy a Raspberry Pi with sensors (temperature, humidity, air quality) in a remote location. Use SSH to periodically retrieve sensor data, update data logging scripts, or adjust sampling rates. * **Automated Plant Watering System:** Monitor soil moisture and control a water pump. SSH enables you to check the system's status, manually trigger watering, or fine-tune watering schedules from your phone or laptop. * **Security Camera System:** Set up a Raspberry Pi with a camera module for surveillance. SSH allows you to securely view live streams, download recorded footage, or configure motion detection settings. * **Remote File Server/NAS:** Turn your Raspberry Pi into a personal cloud storage. SSH with SFTP (Secure File Transfer Protocol) provides an encrypted way to upload and download files, making it a secure alternative to public cloud services for sensitive data. * **Off-Grid Data Logger:** For projects in remote areas without internet, SSH can be used over a local network (e.g., a mobile hotspot) to collect data from the Pi when you're nearby, or even over a cellular modem if configured. For these SSH Raspberry Pi IoT projects, the ability to securely connect, deploy updates, and troubleshoot issues without physical access is invaluable, significantly reducing maintenance overhead and increasing reliability.Monitoring and Managing Your IoT Devices Remotely
Beyond just executing commands, SSH is a gateway to comprehensive remote monitoring and management. For instance, you can: * **Check system health:** Use commands like `htop` (a more interactive `top`), `df -h` (disk space), `free -h` (memory usage), or `vcgencmd measure_temp` (CPU temperature) to monitor your Pi's performance and health. * **Update software:** Regularly updating your Raspberry Pi's operating system and installed packages (`sudo apt update && sudo apt upgrade`) is critical for security and stability. SSH allows you to do this remotely. * **Manage services:** Start, stop, or restart services related to your IoT project (e.g., a web server, a Python script running as a service) using `sudo systemctl start/stop/restart service_name`. * **Transfer files:** Securely upload new scripts, configuration files, or download logged data using `scp` (Secure Copy Protocol) or `sftp` (SSH File Transfer Protocol). For example, `scp /path/to/local/file pi@your_pi_ip:/path/on/pi` to upload, or `scp pi@your_pi_ip:/path/on/pi/file /path/to/local/destination` to download. * **Access logs:** View system logs (`journalctl`, `/var/log/syslog`) or application-specific logs to diagnose issues remotely. The power of SSH lies in its ability to provide a full command-line environment, allowing you to manage your IoT devices with the same granularity as if you were sitting directly in front of them. This level of control is fundamental for maintaining reliable and efficient SSH Raspberry Pi IoT projects in the field.Common SSH Challenges and Solutions in IoT
Even with the best intentions, you might encounter challenges when working with SSH on your Raspberry Pi IoT projects. Here are some common issues and their solutions: * **"Connection Refused":** * **Cause:** SSH server (`sshd`) might not be running on the Pi, or the firewall (`ufw`) is blocking the connection. * **Solution:** Ensure SSH is enabled (`sudo systemctl status sshd`). If using `ufw`, allow the SSH port: `sudo ufw allowThe Future of SSH in IoT Security
As the IoT landscape continues to grow, so does the sophistication of threats targeting connected devices. SSH, with its robust encryption and authentication mechanisms, will remain a cornerstone of IoT security. Future developments in SSH will likely focus on: * **Quantum-Resistant Cryptography:** As quantum computing advances, current cryptographic algorithms may become vulnerable. Future SSH versions will need to integrate quantum-resistant algorithms to maintain long-term security. * **Enhanced Key Management:** More streamlined and secure ways to manage large numbers of SSH keys across vast IoT deployments will be crucial. This includes automated key rotation and centralized key management systems. * **Integration with Zero Trust Architectures:** SSH will increasingly be integrated into Zero Trust security models, where every connection and user is continuously verified, regardless of their location. * **Hardware Security Modules (HSMs):** For highly sensitive IoT applications, using hardware security modules on the Raspberry Pi (or connected via USB) to store private keys can provide an additional layer of tamper-resistant security. The emphasis on E-E-A-T (Expertise, Authoritativeness, Trustworthiness) and YMYL (Your Money or Your Life) principles is particularly relevant here. Inadequate security in IoT can lead to severe consequences, from data breaches and privacy violations to physical security risks if devices are compromised. Therefore, understanding and implementing strong SSH security practices is not just about convenience but about safeguarding your data, your privacy, and potentially even physical assets connected to your IoT network. The continuous evolution of SSH will play a vital role in ensuring that SSH Raspberry Pi IoT projects remain secure and resilient against emerging threats.Conclusion
SSH is an indispensable tool for anyone venturing into SSH Raspberry Pi IoT projects. It provides the secure, remote access necessary to deploy, manage, and troubleshoot devices scattered across various locations. From the initial setup to implementing advanced security measures like key-based authentication and non-standard ports, understanding SSH best practices is paramount for building robust and resilient IoT solutions. We've explored how to maintain persistent connections, decipher SSH algorithms, and tackled common challenges, ensuring your projects run smoothly and securely. The power of the Raspberry Pi combined with the security of SSH opens up a world of possibilities for innovation, from smart homes to environmental monitoring and beyond. By prioritizing security and leveraging the full capabilities of SSH, you're not just building functional devices; you're building trustworthy and future-proof IoT ecosystems. What are your favorite SSH tips or Raspberry Pi IoT projects? Share your experiences and insights in the comments below, or explore our other articles for more guides and inspiration to further enhance your IoT journey!Related Resources:
Detail Author:
- Name : Prof. Eino Funk
- Username : pierre44
- Email : alivia42@larkin.com
- Birthdate : 1990-10-09
- Address : 52745 Kilback Parkways North Genoveva, NY 37131
- Phone : (623) 515-1308
- Company : Gaylord-Cormier
- Job : Paste-Up Worker
- Bio : Pariatur quaerat beatae minus aut numquam ut. Perspiciatis pariatur doloribus cupiditate ducimus repudiandae. Reprehenderit quas in velit aut officia suscipit. Quia nesciunt enim aliquam nulla sint.
Socials
instagram:
- url : https://instagram.com/kmiller
- username : kmiller
- bio : Reprehenderit distinctio qui et et in id nihil. Occaecati sit nobis voluptatem alias quis.
- followers : 840
- following : 927
linkedin:
- url : https://linkedin.com/in/miller1976
- username : miller1976
- bio : Sed quas dicta mollitia.
- followers : 2255
- following : 2316
twitter:
- url : https://twitter.com/karen.miller
- username : karen.miller
- bio : Aut sunt aperiam rerum quod minima. Et et iure voluptates cumque repudiandae. Quisquam est cum dolorem. Consectetur omnis enim ab ut ducimus.
- followers : 1764
- following : 645
facebook:
- url : https://facebook.com/karenmiller
- username : karenmiller
- bio : Officia consectetur dolores velit. Ipsa qui minima nulla beatae velit.
- followers : 2191
- following : 1690